SolarWinds Makes It Easy to Detect SharePoint Breaches with Integration to LOGbinder SP
Mon, 07 Jul 2014 08:40:59 GMT
SolarWinds Log and Event Manager provides connectors for common log sources that understand how to translate raw events from a specific log source into their equivalent normalized event type. I love event normalization like SolarWind’s LEM because it makes it so much easier to correlate events from multiple sources and to configure more generalized alerts, filters and reports. For instance you can just ask for all logon failures without having to configure criteria for every example of logon failure logged by Windows, Linux, firewalls, etc. That’s the power of normalization.
SharePoint security is getting more and more attention because of the amount of sensitive unstructured data found there. And with SharePoint’s self-service features sensitive data just keeps growing as end-users create more and more content. In this age of Snowden-like information grabs it’s really important to detect unusual activity in SharePoint.
But getting SharePoint logs into any SIEM is not a simple matter. SharePoint audit logs are trapped inside SharePoint itself; there’s no log file or event log that a SIEM can consume through normal means. Happily SolarWinds partnered with LOGbinder and has done an awesome job integrating with LOGbinder SP. LOGbinder SP is an easy-to-deploy middleware purpose built to pull raw audit events out of SharePoint, translate all the cryptic codes and ID numbers and then export understandable audit logs which can be easily consumed by SIEMs through normal log collection means.
Not only did SolarWinds create the necessary connector to consume SharePoint audit events from LOGbinder. But as a SIEM Synergy Partner, SolarWinds took my recommended reports and alert specs for SharePoint and implemented them in a set of Filters, Rules and Reports for Log and Event Manager. All you have to do is point Log and Event Manager at LOGbinder SP’s event log and you’ve got real-time monitoring and historical analysis of the Share Point security activity.
Check out the screen print below showing SharePoint permission changes in Log and Event Manager.

And below is an example report showing document deletions in a SharePoint Document Library.

Here’s a list of some of the things in SharePoint you can automatically monitor or detect with Log and Event Manager:
SolarWinds did a great job implementing our monitoring and reporting recommendations, but thanks to Log and Event Manager’s (LEM) event normalization you can also correlate SharePoint audit events with similar audit activity from other log sources. For instance you can search on a given user and see their activity as reported by SharePoint, Active Directory and any other log sources managed by LEM. To learn more about LEM’s normalization and other features check out this blog http://www.ultimatewindowssecurity.com/blog/default.aspx?p=a27fadf5-b1d2-4216-a444-f60d496ab99c or download Log and Event Manager here http://www.solarwinds.com/register/registrationb.aspx?program=1520&c=70150000000PExs. You can download a trial of LOGbinder SP from http://www.logbinder.com/Form/LBSPDownload and the integration pack for LEM and LOGbinder SP here http://thwack.solarwinds.com/docs/DOC-167091. Try them out!
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
Live with Dell at RSA 2015
Severing the Horizontal Kill Chain: The Role of Micro-Segmentation in Your Virtualization Infrastructure
5 Indicators of Endpoint Evil
Audit Myth Busters: SharePoint, SQL Server, Exchange
Wed, 02 Oct 2013 08:44:19 GMT
Had many, many valuable conversations with colleagues in DC a couple weeks ago at HP Protect 2013 about auditing and monitoring SharePoint, SQL Server and Exchange. This is a tough subject because there are so many details. You can’t just answer "Are you currently monitoring SharePoint/SQL/Exchange: Yes/No?"
This is because each of those applications have multiple logs with widely ranging security value and content. Also, there are some existing connectors from HP for these apps but their capabilities, caveats vary greatly - as well as exactly which logs and versions of SharePoint/SQL/Exchange they apply to. Many folks are making decisions and/or belaboring under one or more misconceptions.
In this post I'm going to try to quickly bust a few of those and myths and provide links to where you can get more details. It’s kind of specific to ArcSight users but has value to anyone with a SIEM and Microsoft apps.
1. We are already monitoring SharePoint.
OK, but what are you actually monitoring in SharePoint? SharePoint has about 4 different logs. Only one of them is the actual SharePoint Audit Log with security activity. And that log is not available through normal log collection means. Just recently HP released a SmartConnector for SharePoint. But this SmartConnector simply uses JDBC to pull the raw audit log from the SharePoint DB. Take a look at the raw audit log in SharePoint (http://www.ultimatewindowssecurity.com/sharepoint/logbindersp/crypticdata.aspx) Getting the raw SharePoint audit log into ArcSight allows you to say you are collecting the SharePoint Audit log but try understanding and responding to the events. Things like user 17 and role 42 are not translated, so you don’t know who or what you are dealing with. Check here for more non-commercial information on the SharePoint audit log. Learn how we solve the problem with LOGbinder SP here.
2. We are already monitoring Exchange.
Again, what are you actually getting from Exchange? Exchange has 3 different logs that are valuable to security. The message tracking log tracks message flow and is available through a connector for Exchange Message tracking. While it’s incredibly voluminous, it does allow you to track all inbound and outbound emails, but it doesn’t track:
- Non-owner access to other mailboxes
- Mailbox copies and exports
- Privileged user operations
- Administrative changes
- Security policy and configuration changes
For non-owner mailbox access auditing, you need the mailbox audit log. As of Exchange 2010 that log is not a log file nor is it sent to the Windows event log. Each mailbox has a hidden folder where it stores audit records for that mailbox. There is a SmartConnector for the Exchange mailbox audit log and it is practical if you need to audit a handful of mailboxes and do not require full audit log integrity. See my comparison here between that SmartConnector and LOGbinder EX. Check here for more non-commercial information on the mailbox audit log.
The 3rd log in Exchange, admin audit log, is extremely important because it gives a full fidelity audit trail of all privileged user activity in Exchange including:
- Exports and copies of mailboxes
- Changes to security policies
- and about 600 other operations
This log is also completely inaccessible to SIEMs because it’s stored in a hidden mailbox of all places in Exchange. There is no connector at all, but we do handle it beautifully with LOGbinder EX. Check here for more non-commercial information on the admin audit log.
What about SQL Server auditing?
SQL Server 2008 added a new and beautiful, true, honest-to-goodness audit capability. It blows the old SQL Trace out of the water. No comparison. SQL Audit can send events directly to the Windows event log which you could then pick up with the WUC or Snare, etc. But if your DB admin has anything to do with it you may run into trouble because of the performance load of both logging and retrieving those events through the heavy Windows event API. Microsoft recommends using the other output option which is to a binary log file on some other server on the network. This is the most efficient high speed low overhead method of getting audit events off of a busy production SQL Server. If you need that option, LOGbinder SQL is there to help. The other issue with collecting SQL audit events from the Windows event log is that SQL Server logs every possible operation (we’re talking 100s of them) as just one generic event ID with the same static text and fields. Can you say cryptic? We can help with that too. More, non-commercial, information on SQL Server Audit here.
Some other educational resources right here on 724 are: https://protect724.arcsight.com/docs/DOC-3181 for Exchange and https://protect724.arcsight.com/docs/DOC-3170 for SharePoint.
I hope this helps and feel free to reach out to me anytime…
Randy Franklin Smith
Security Log Nerd
Designer of LOGbinder
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (1)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
Audit Myth Busters: SharePoint, SQL Server, Exchange
How to Audit Privileged Operations and Mailbox Access in Office 365 Exchange Online
LOGbinder SQL Beta is released! Join beta testers now
New Whitepaper by Randy Franklin Smith "Comparing SharePoint's 4 Audit Logs for Security and SIEM Integration"
Sat, 24 Nov 2012 18:30:31 GMT
This whitepaper by Randy Franklin Smith, provides an overview of the 4 different
logs in SharePoint and discusses their relative merits in terms of security
value and how to integrate with your SIEM.
Click here to download it now.
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
5 Indicators of Endpoint Evil
Severing the Horizontal Kill Chain: The Role of Micro-Segmentation in Your Virtualization Infrastructure
Anatomy of a Hack Disrupted: How one of SIEM’s out-of-the-box rules caught an intrusion and beyond
New Whitepaper: SharePoint Audit Logging with HP ArcSight and LOGbinder SP
Tue, 06 Nov 2012 17:19:28 GMT
Over at LOGbinder we've released a new whitepaper explaining how LOGbinder SP is the only recognized solution for providing reliable audit information about the security events of SharePoint via HP ArcSight and how it works with many other SIEMs.
Did you know that SharePoint generates several different logs ranging from true audit logs to diagnostic trace logs and usage analysis? This brief will identify what (if any) security intelligence can be learned from each log. It will then explain which logs are readily available to SIEMs, and which logs are not readily available.
Click here to download the whitepaper.
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Live with Dell at RSA 2015
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
Understanding the Difference between “Account Logon” and “Logon/Logoff” Events in the Windows Security Log
Live with LogRhythm at RSA
UltimateWindowsSecurity.com 2.0: New Coverage for SQL Server and SharePoint audit logging
Wed, 13 Jun 2012 16:38:43 GMT
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
5 Indicators of Endpoint Evil
Severing the Horizontal Kill Chain: The Role of Micro-Segmentation in Your Virtualization Infrastructure
Anatomy of a Hack Disrupted: How one of SIEM’s out-of-the-box rules caught an intrusion and beyond
Recommended Alerts and Reports for SharePoint (LOGbinder SP) Updated
Wed, 18 Apr 2012 12:15:00 GMT
I'm happy to let you know that with the recent release of LOGbinder SP 3.0 I've updated our Recommended Alerts and Reports for SharePoint (LOGbinder SP) which you can find at http://www.logbinder.com/Resources/.
Updates include
- coverage of new events and features in LOGbinder SP 3.0.
- new recommended alert rules
- important notes and explanations regarding "insertion strings", how date/time works in LOGbinder SP and information about the 2 possible "event log sources" that LOGbinder SP events can bear.
This free resource is valuable for anyone looking for tips and recommendations on creating reports or alert rules for SharePoint audit events.
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
5 Indicators of Endpoint Evil
Live with Dell at RSA 2015
Live with LogRhythm at RSA
How to Audit an Individual Library or List in SharePoint
Wed, 22 Jun 2011 18:24:46 GMT
SharePoint audit policy is widely regarded as a site collection level setting leading many to believe you must apply one audit policy to all objects in the entire site collection. If that were the case you would run into some real granularity problems leading to either not being able to get the events you need for important lists or libraries or else enabling too much auditing and getting way to many events.
Thankfully though you can enable auditing on specific document libraries or lists but you have to know where to look which I will explain in a moment.
First though what audit policies would you likely want to enable for an entire site collection and what would you want to activate only on specific lists and libraries? The one audit policy I always suggest enabling "Editing users and permissions" (aka Security Change in LOGbinder SP) which will provide an audit trail of all auditable security related changes for the site collection including permission changes, changes to users and groups and change to audit policy itself.
At the list and library level you have a variety of activities you that you can audit including:
- Viewing
- Editing
- Deletion
- Check in /Check out
List/library level audit policy is extremely important when it comes to auditing who is viewing confidential information. If you enable View auditing at the site collection level you end up generating events for every page click by every user througout the entire site collection which will create a load on resources and storage.
To enable auditing for a certain library access the library’s (or list’s) settings page and click the “Information management policy settings” link under Permissions and Management.
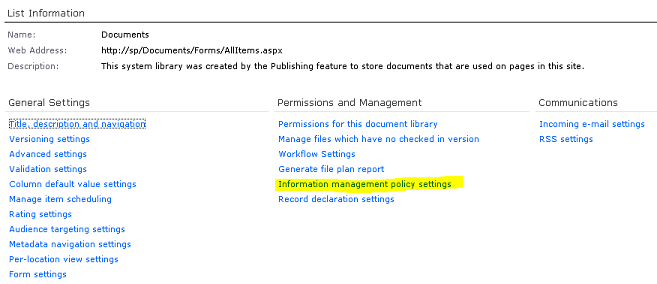
In the next page you’ll see entries for the content types allowed for that list
or library. For instance a normal document library will have 2 content types:
Document and Folder. Click on a content type and configure auditing. In the
example below I’ve enabled auditing of any type of view and download access
since this is a library contains confidential information.
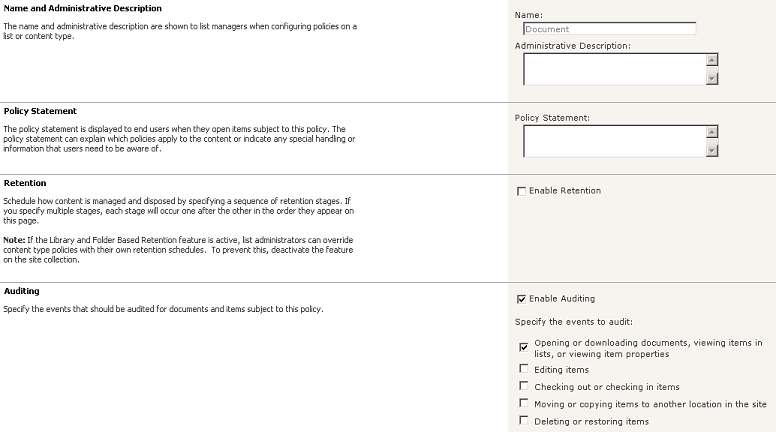
Now SharePoint will obediently begin auditing those actions on that particular list or library and if you have my LOGbinder SP software you'll be able to report or alert on those events with LOGbinder SP SIEM Edition or if you have your own log management / SIEM solution you can use LOGbinder SP Agent Edition to get SharePoint audit events out of the content database where they don't belong and into your log management solution where they do! Click here for more information on LOGbinder SP.
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
5 Indicators of Endpoint Evil
Severing the Horizontal Kill Chain: The Role of Micro-Segmentation in Your Virtualization Infrastructure
Anatomy of a Hack Disrupted: How one of SIEM’s out-of-the-box rules caught an intrusion and beyond
Making the SharePoint Audit Log Usable
Tue, 09 Feb 2010 10:53:22 GMT
As more and more information and processes move to SharePoint, it becomes critical for compliance and security requirements to monitor and audit SharePoint activity.
I was very excited when I first learned about the SharePoint audit log but I quickly determined that in its unimproved state the SharePoint audit log is essentially unusable due to 4 key issues:
- SharePoint's audit log does not provide the names of users or objects.
The SharePoint audit log fails to translate record IDs, meaning you have no idea what object or user to which a given event refers! Click here for an example of an audit event from SharePoint and then what LOGbinder does with it.
- SharePoint's audit log is buried in SharePoint's SQL server content database.
To ensure the integrity of audit trails, logs must be moved from the system where they are generated to separate and security log archive. However in SharePoint, the audit log isn't really a log - it's a table in the SharePoint database. This makes it inaccessible for most log management solutions. Without the ability to collect the SharePoint audit log into a separate, secure log archive its value as a high integrity audit trail is compromised.
- SharePoint's audit log has no reporting.
In Windows Sharepoint Services the log is totally inaccessible and in Office Sharepoint Services it's exposed through through a few rudimentary, impractical reports in Excel.
- Windows SharePoint Services provides no interface for enabling auditing at all.
The audit log is there but without custom programming there's no way to turn it on; much less access the logs.
I'm still a software developer at heart and the problems with the SharePoint audit log finally pushed me over the edge. The result is LOGbinder SP.
LOGbinder SP is a small, efficient Windows service that monitors the internal SharePoint audit log without making any changes to your SharePoint installation.
For each event LOGbinder SP resolves the user and object IDs and other cryptic codes, producing an easy to understand, plain-English translation of the SharePoint audit event. LOGbinder SP then sends these events to the Windows event log (either the Security log or a custom log) which in turn allows you to leverage any log management solution to collect, monitor, alert, analyze, report and archive SharePoint audit logs.
Here's an example event from the SharePoint audit log pictured as delivered via Excel compared to what the event looks like after LOGbinder SP translates it.
LOGbinder SP turns this:
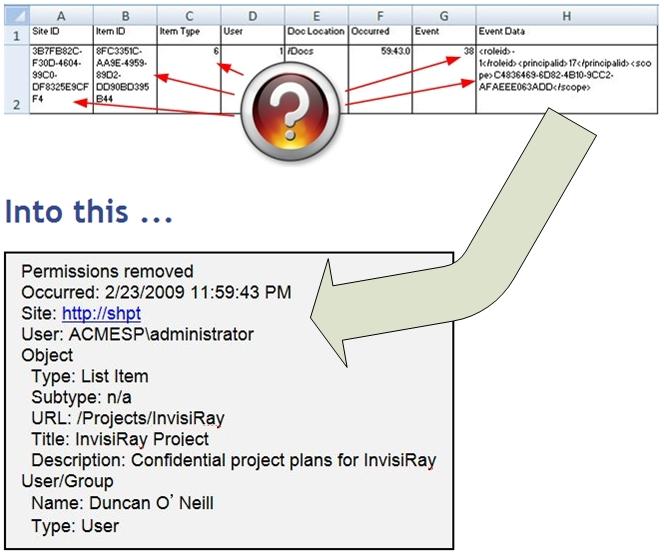
LOGbinder SP is now out of beta and ready for prime-time. You can download an evaluation copy, watch a webinar on the SharePoint audit log, get your questions answered and more at: www.logbinder.com
Please try it out and tell me what you think!
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
Understanding the Difference between “Account Logon” and “Logon/Logoff” Events in the Windows Security Log
5 Indicators of Endpoint Evil
Audit Myth Busters: SharePoint, SQL Server, Exchange
New Software that Unlocks the SharePoint Audit Log
Thu, 24 Sep 2009 10:08:14 GMT
I am very excited today to announce the beta release of LOGbinder SP - my first software solution aimed at expanding the reach of log management.
LOGbinder SP allows you to audit security events in SharePoint with the Windows Security Log.
Why do I need LOGbinder SP? Doesn't SharePoint already have an audit log?
LOGBinder SP is a small, efficient .NET service that monitors the internal SharePoint audit log. For each event LOGbinder SP resolves the user and object IDs and other cryptic codes, producing an easy to understand, plain-English translation of the SharePoint security event. (Click here for a list of events.) Then LOGbinder SP forwards the event to one or more output formats:
- local Windows security event log
- custom Windows event log
- syslog server*
- text file*
- XML file*
- SQL server reporting database*
This variety of output formats allows you to extend any log management solution to now support SharePoint audit trails and security events.
Alternatively, or in addition to integrating with your log management solution, you configure LOGbinder SP to send events to a SQL Server reporting databse and use our pre-built reports (implemented in SQL Reporting Services) to review and analyze the security activity of your SharePoint sites.
LOGbinder SP is currently in beta and available as a free download. Please help us build LOGbinder SP into a great solution!
Please visit http://www.logbinder.com/Products/LOGbinderSP/ to learn more about the SharePoint audit log and it's woeful limitations and how we fix them with LOGbinder SP.
Please download and put LOGBinderSP to work for you, securing SharePoint data.
* not yet implemented in the current beta
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
Live with Dell at RSA 2015
5 Indicators of Endpoint Evil
Understanding the Difference between “Account Logon” and “Logon/Logoff” Events in the Windows Security Log
previous | next
powered by Bloget™