«
Pay Attention to System S... |
New Technical Brief by Ra... »
Using Dynamic Audit Policy to Detect Unauthorized File Access
Tue, 15 Oct 2013 13:43:49 GMT
This article was first published in EventTracker’s EventSource Newsletter: http://www.eventtracker.com/newsletters/using-dynamic-audit-policy-to-detect-unauthorized-file-access/
One thing I always wished you could do in Windows auditing was mandate that access to an object be audited if the user was NOT a member of a specified group. Why? Well sometimes you have data that you know a given group of people will be accessing and for that activity you have no need of an audit trail.
Let’s just say you know that members of the Engineering group will be accessing your Transmogrifier project folder and you do NOT need an audit trail for when they do. But this is very sensitive data and you DO need to know if anyone else looks at Transmogrifier.
In the old days there was no way to configure Windows audit policy with that kind of negative Boolean or exclusive criteria. With Windows 2008/7 and before you could only enable auditing based on if someone was in a group not the opposite.
Windows Server 2012 gives you a new way to control audit policy on files. You can create a dynamic policies based on attributes of the file and user. (By the way, you get the same new dynamic capabilities for permissions, too).
Here’s a screen shot of audit policy for a file in Windows 7.
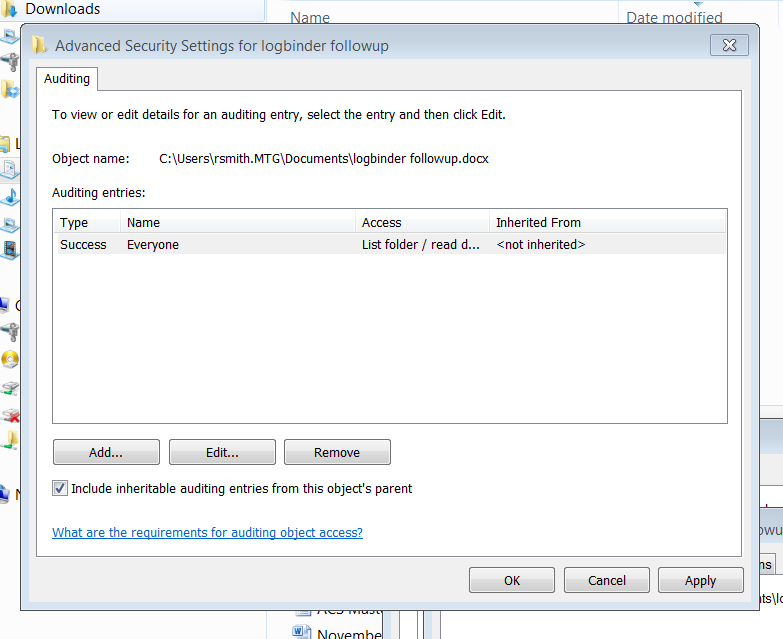
Now compare that to Windows Server 2012.
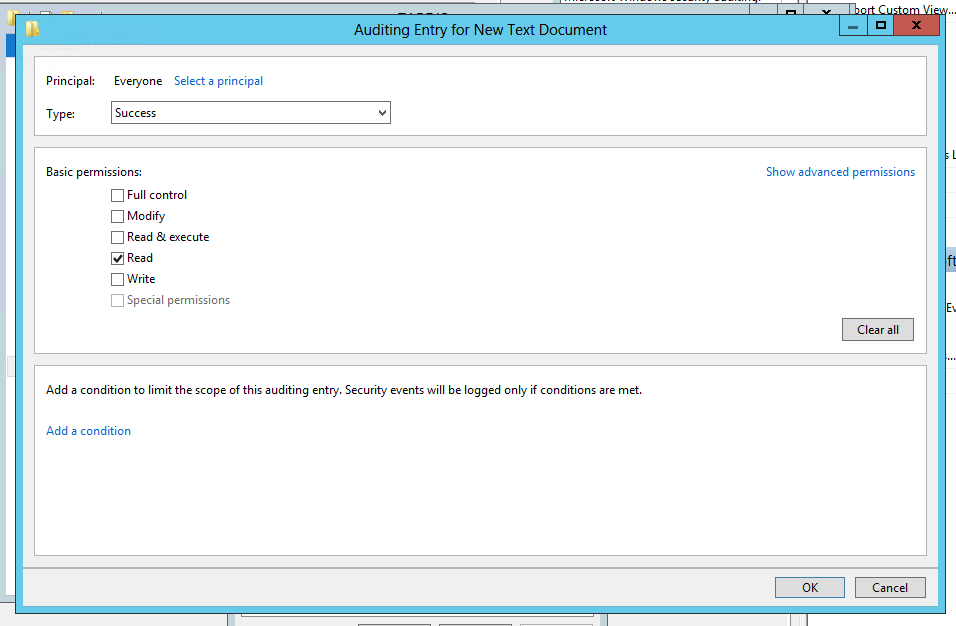
The same audit policy is defined but look at the “Add a condition” section. This allows you to add further criteria that must be met before the audit policy takes effect. Each time you click “Add a condition” Windows adds another criteria row where you can add Boolean expressions related to the User, the Resource (file) being accessed or the Device (computer) where the file is accessed. In the screen shot below I’ve added a policy which accomplishes what we described at the beginning of the article.
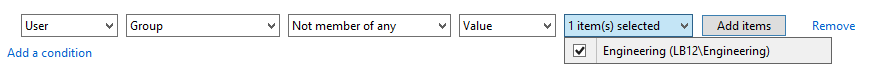
So we start out by saying that Everyone is audited when they successfully read data in this file. But then we limit that to users who do not belong to the Engineering group. Pretty cool, but we are only scratching the surface. You can add more conditions and you can join them by Boolean operators OR and AND. You can even group expressions the way you would with parenthesis in programming code. The example below shows all of these features so that the audit policy is effective if the user is either a member of certain group or department is Accounting and the file has been classified as relevant to GLBA or HIPAA compliance.
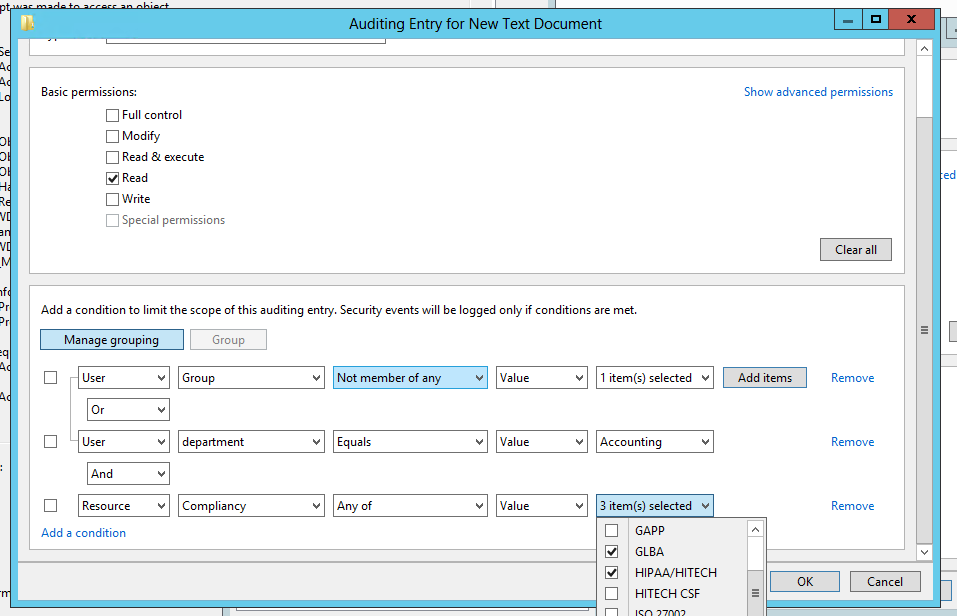
You’ll also notice that you can base auditing and access decision on much more that the user’s identity and group membership. In the example above we are also referencing the department specified on the Organization tab of the user’s account in Active Directory. But with dynamic access control we can choose any other attribute on AD user accounts by going to Dynamic Access Control in the Active Directory Administrative Center and selecting Claim Types as shown here.
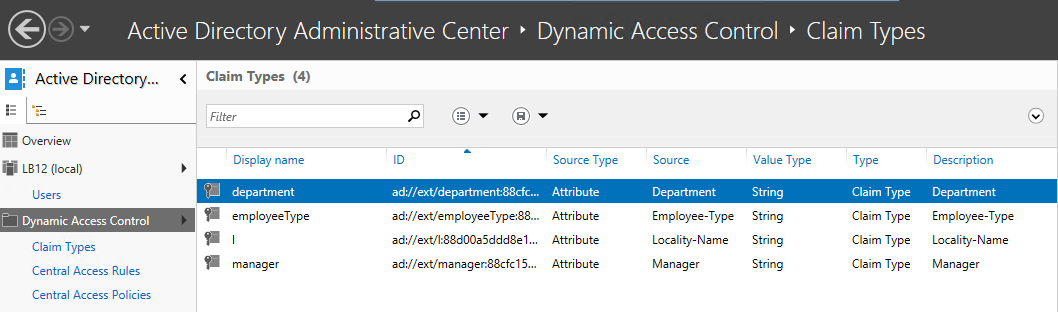
You can create claim types for about any attribute of computer and user objects. After creating a new claim type for a given attribute, it’s available in access control lists and audit policies of files and folders throughout the domain.
But dynamic access control and audit policy doesn’t stop with sophisticated Boolean logic and leveraging user and computer attributes from AD. You can now classify resources (folders and files) according to any number of properties you’d like. Below is a list of the default Resource Properties that come out of the box.
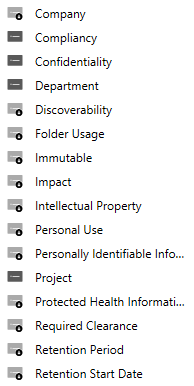
Before you can begin using a given Resource Property in a dynamic access control list or audit policy you need to enable it and then add it to a Resource Property List which is shown here.
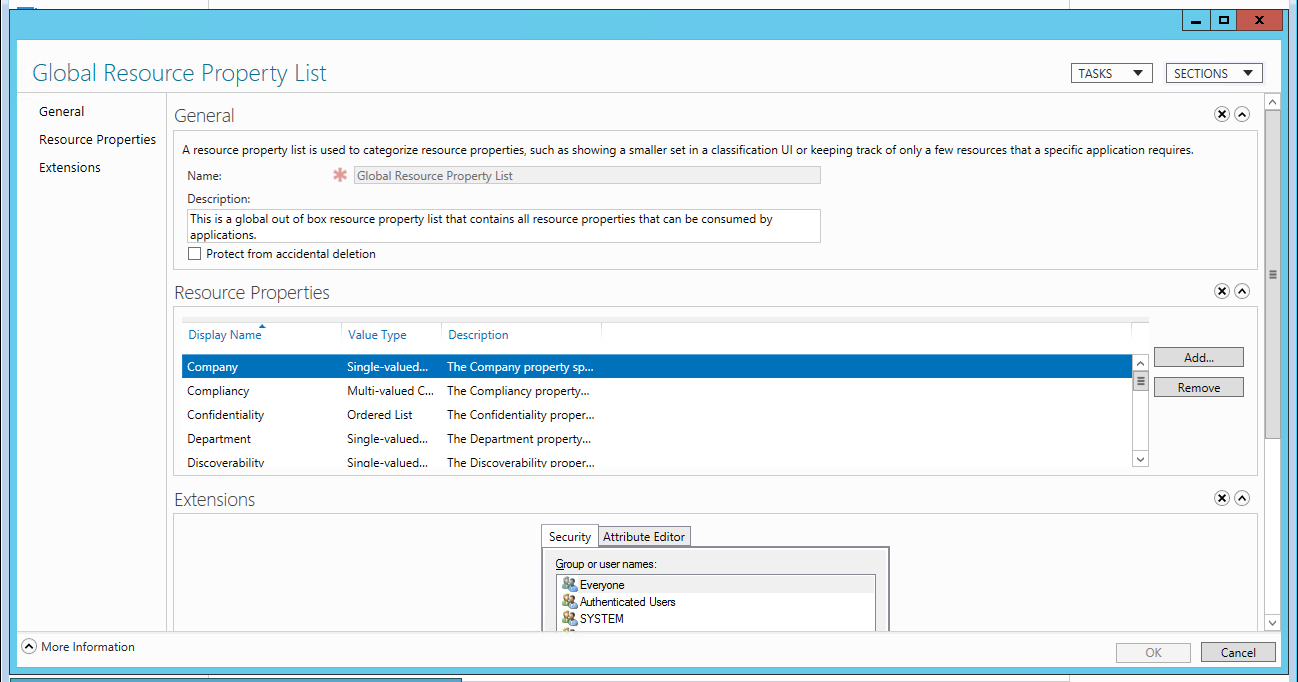
After that you are almost ready to define dynamic permissions and audit policies. The last setup step is to identity file servers where you want to use classify files and folders with Resource Properties. On those file servers you need to add the File Server Resource Manager subrole. After that when you open the properties of a file or folder you’ll find a new tab called Classification.
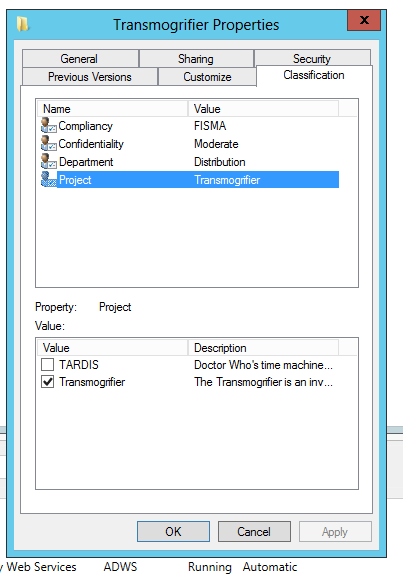
Above you’ll notice that I’ve classified this folder as being related to the Transmogrifier project. Be aware that you can define dynamic access control and audit policies without referencing Resource Properties or adding the File Server Resource Manager subrole; you’ll just be limited to Claim Types and the enhanced Boolean logic already discussed.
The only change to the file system access events Windows sends to the Security Log is the addition of a new Resource Attributes to event ID 4663 which I’ve highlighted below.
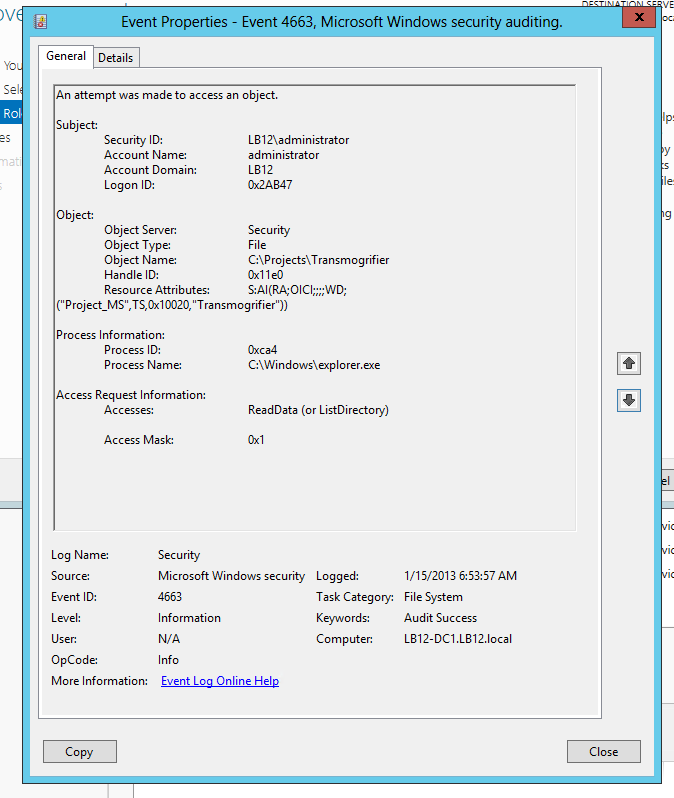
This field is potentially useful in SIEM solutions because it embeds in the audit trail a record of how the file was classified when it was accessed. This would allow us to classify important folders all over our network as “ACME-CONFIDENTIAL” and then include that string in alerts and correlation rules in a SIEM like EventTracker to alert or escalate on events where the information being accessed has been classified as such.
The other big change to auditing and access control in Windows Server 2012 is Central Access Policies which allows you to define a single access control list or audit policy in AD and apply it to any set of computers. That policy is now evaluated in addition to the local security descriptor on each object.
While Microsoft and press are concentrating on the access control aspect of these new dynamic and central security features, I think the greatest immediate value may come from the audit policy side that we’ve just explored. If you’d like to learn more about dynamic and central access control and audit policy check out the deep dive session I did with A.N. Ananth of EventTracker: File Access Auditing in Windows Server 2012.
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
5 Indicators of Endpoint Evil
Severing the Horizontal Kill Chain: The Role of Micro-Segmentation in Your Virtualization Infrastructure
Live with Dell at RSA 2015
Comments disabled
powered by Bloget™