 Windows Security Log Event ID 4704
Windows Security Log Event ID 4704

| Operating Systems |
Windows 2008 R2 and 7
Windows 2012 R2 and 8.1
Windows 2016 and 10
Windows Server 2019 and 2022
|
Category
• Subcategory | Policy Change
• Authorization Policy Change |
|
Type
|
Success
|
Corresponding events
in Windows
2003
and before |
608
|
4704: A user right was assigned
On this page
This event documents a change to user right assignments on this computer including the right and user or group that received the new right.
Note: "User rights" and "privileges" are synonymous terms used interchangeably in Windows.
Rights, like most other security settings, are defined in group policy objects and applied by the computer. Therefore this event will normally show the Assigned By user as the system itself. To determine who actually made the rights assignment change you must search the domain controllers' security logs for changes to groupPolicyContainer objects (logged by Directory Service auditing).
Logon ID allows you to link this event to the prior event 4624 logon event of the user who performed this action.
Note: This event, 4704, and 4705 do not log changes to logon rights such as "Access this computer from the network" or "Logon as a service". See events 4717 and 4718.
User Rights
|
System name
|
Description
|
|
SeTcbPrivilege
|
Act as part of the operating system
|
|
SeMachineAccountPrivilege
|
Add workstations to domain
|
|
SeIncreaseQuotaPrivilege
|
Adjust memory quotas for a process
|
|
SeBackupPrivilege
|
Back up files and directories
|
|
SeChangeNotifyPrivilege
|
Bypass traverse checking
|
|
SeSystemtimePrivilege
|
Change the system time
|
|
SeCreatePagefilePrivilege
|
Create a pagefile
|
|
SeCreateTokenPrivilege
|
Create a token object
|
|
SeCreatePermanentPrivilege
|
Create permanent shared objects
|
|
SeDebugPrivilege
|
Debug programs
|
|
SeEnableDelegationPrivilege
|
Enable computer and user accounts to be trusted for delegation
|
|
SeRemoteShutdownPrivilege
|
Force shutdown from a remote system
|
|
SeAuditPrivilege
|
Generate security audits
|
|
SeIncreaseBasePriorityPrivilege
|
Increase scheduling priority
|
|
SeLoadDriverPrivilege
|
Load and unload device drivers
|
|
SeLockMemoryPrivilege
|
Lock pages in memory
|
|
SeSecurityPrivilege
|
Manage auditing and security log
|
|
SeSystemEnvironmentPrivilege
|
Modify firmware environment values
|
|
SeManageVolumePrivilege
|
Perform volume maintenance tasks
|
|
SeProfileSingleProcessPrivilege
|
Profile single process
|
|
SeSystemProfilePrivilege
|
Profile system performance
|
|
SeUndockPrivilege
|
Remove computer from docking station
|
|
SeAssignPrimaryTokenPrivilege
|
Replace a process level token
|
|
SeRestorePrivilege
|
Restore files and directories
|
|
SeShutdownPrivilege
|
Shut down the system
|
|
SeSyncAgentPrivilege
|
Synchronize directory service data
|
|
SeTakeOwnershipPrivilege
|
Take ownership of files or other objects
|
Free Security Log Resources by Randy
Subject:
The ID and logon session of the user that assigned the right. Unfortunately this is just the local system account - see above.
- Security ID: The SID of the account.
- Account Name: The account logon name.
- Account Domain: The domain or - in the case of local accounts - computer name.
- Logon ID is a semi-unique (unique between reboots) number that identifies the logon session. Logon ID allows you to correlate backwards to the logon event (4624) as well as with other events logged during the same logon session.
Target Account:
The user or group that was assigned the right. Account Name: name of user or group
New Right:
User Right: the name of the right assigned - user rights table above
Supercharger Free Edition
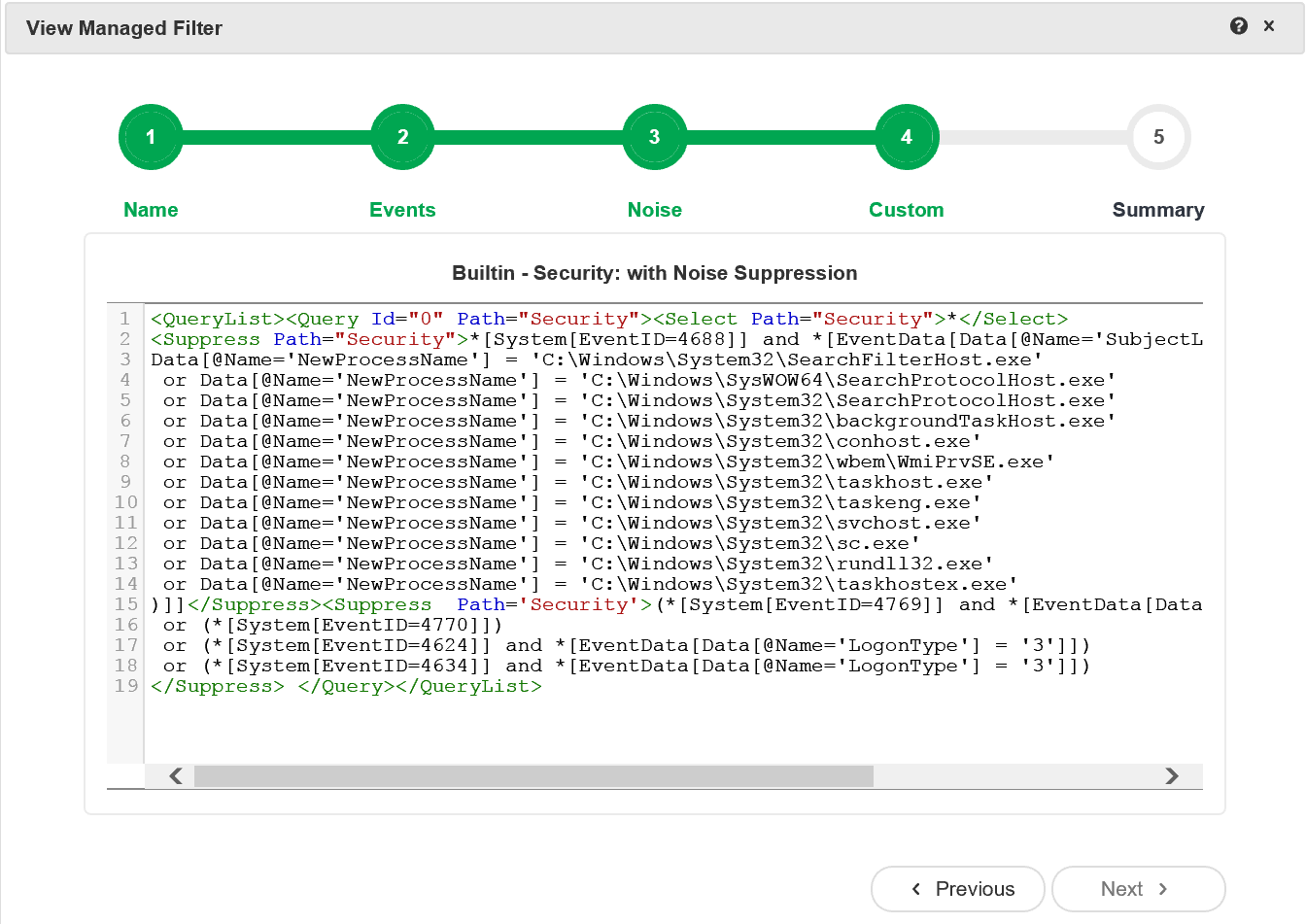
Supercharger's built-in Xpath filters leave the noise behind.
Free.