WinSecWiki > Security Settings > Local Policies > Audit Policy > Object Access
Audit Object Access
The Audit object access policy handles auditing access to all objects outside AD. The first use you might think of for the policy is file and folder auditing, but you can use it to audit access to any type of Windows object including registry keys, printers, and services. Furthermore, auditing access to an object such as a crucial file requires you to enable more than just this category; you must also enable auditing for the specific objects you want to track. To configure an object’s audit policy, open the object's Properties, select the Security tab, click Advanced, and then select the Auditing tab. Be warned: This policy can really bog down your server if you enable it on too many objects.
The following is an excerpt from my book , The Windows Security Log Revealed :
You can use the Object Access Security log category to audit any and all attempts to access files and other Windows objects. The only auditable objects not covered by this category are AD objects, which you can track by using the Directory Service category. In addition to tracking files, you can track success and failure access attempts on folders, services, registry keys, and printer objects. The way in which you define Object Access audit policy and the format of information recorded in the Security log for this category are closely related to the structure of the ACLs that all objects use to define who can access the object and how.
When you enable the Audit object access events policy for a given computer, Windows doesn’t immediately begin auditing all access events for all objects because the system would immediately grind to a halt. Activating object access auditing is a two-step procedure. First, enable the Audit object access events policy on the system that contains the objects you want to monitor. Second, select specific objects and define the types of access you want to monitor. you make these selections in the object’s audit settings, which you’ll find on the object's Advanced Security Settings dialog box. For instance, Figure 7-1 displays the audit settings for a folder named Accounting Data.
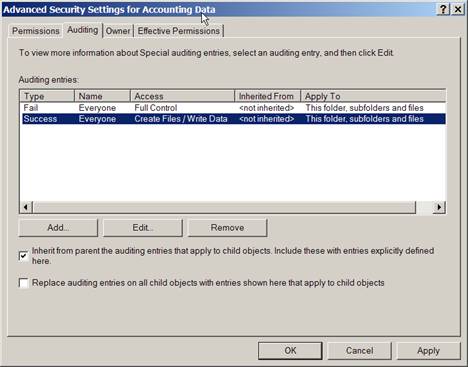
Figure 7‑1 Object audit policy
|
For a list of Event IDs generated by this category, see the Security Log Encyclopedia.
Bottom Line
- Windows XP, 2000 and 2003: I don’t recommend enabling this policy unless you have specific objects and permissions types planned for auditing.
- Windows Server 2008 and Vista: I don't recommend managing audit policy at this level because too much noise is generated. Use subcategories instead. See Audit Category: Object Access (Windows Server 2008 and Vista).
Child articles:
Back to top