WinSecWiki > Security Settings > Local Policies > Audit Policy > DS Access
Directory Service Access
The Audit directory service access policy provides a low-level audit trail of changes to objects in AD. The policy tracks the same activity as Audit account management events, but at a much lower level. By using this policy, you can identify exactly which fields of a user account or any other AD object were accessed. Audit account management events provides better information for monitoring maintenance to user accounts and groups, but Audit directory service access is the only way to track changes to OUs and GPOs, which can be important for change-control purposes.
The following is an excerpt from my book , The Windows Security Log Revealed :
Whereas Account Management events provide excellent auditing of user, group, and computer maintenance, Directory Service Access events make low-level auditing available for all types of objects in AD. Directory Service Access events not only identify the object that was accessed and by whom but also document exactly which object properties were accessed. Directory Service Access events work a lot like Object Access events because you must first enable the audit policy at the system level, then activate auditing on the specific objects you want to monitor. To enable auditing on a file, open the file’s Properties dialog box from within Windows Explorer, select the Security tab, click Advanced, and then select the Auditing tab on the Advanced Security Settings dialog box. To enable auditing on an AD object, follow the same path but from within the Active Directory Users and Computers snap-in (rather than Windows Explorer), as Figure 9-1 shows. Then, specify the permissions you want to audit when users request access to the object.
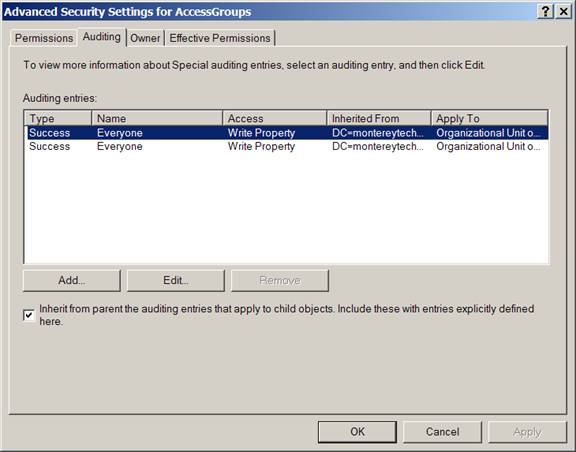
Figure 9‑1 Audit policy for an OU
|
At this point, the procedure for auditing AD objects diverges a bit from file-system auditing. For files, you simply select auditing for the permissions that can be performed against the file. However, AD has two types of operations: operations performed against the object, and Read and Write operations against individual properties of the object. These two types of operations correspond to the Object and Properties tabs that Figure 9‑2 shows.
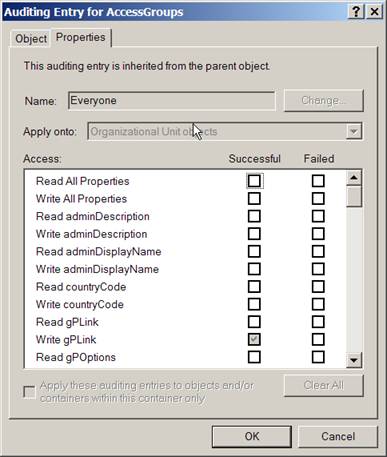
Figure 9‑2 Auditing entry for an OU
|
For a list of Event IDs generated by this category, see the Security Log Encyclopedia.
Bottom Line
-
Windows XP, 2000 and 2003: I recommend enabling this policy for success on domain controllers as well as enabling auditing on the root of the domain, OUs and GPOS for modification of important properties.
- Windows Server 2008 and Vista: I don't recommend managing audit policy at this level because too much noise is generated. Use subcategories instead. See Audit Category: DS Access (Windows Server 2008 and Vista ).
Child articles:
Back to top