 Sysmon Event ID 28
Sysmon Event ID 28

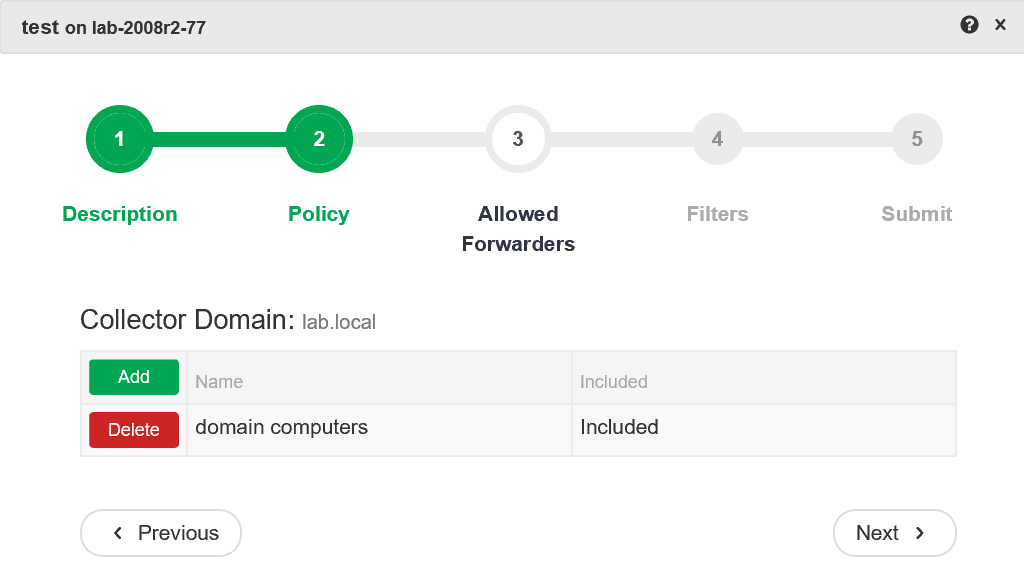
28: File Block Shredding
This is an event from
Sysmon.
On this page
Good attackers clean up after themselves by deleting files which you can block with Event ID 23 or just catch with Event ID 26. But even better attacks destroy (overwrite) the actual content of deleted files with a tool like sdelete in a technique commonly called "shredding". This is another Sysmon event that actively blocks activity. There is no detect only version of this event.
Free Security Log Resources by Randy
- Log Name
- Source
- Date
- Event ID
- Task Category
- Level
- Keywords
- User
- Computer
- Description
- RuleName
- UtcTime
- ProcessGuid
- ProcessId
- User
- Image
- TargetFilename
- Hashes
- IsExecutable
Supercharger Free Edition
Centrally manage WEC subscriptions.
Free.
Log Name: Microsoft-Windows-Sysmon/Operational
Source: Microsoft-Windows-Sysmon
Date: 4/15/2024 8:57:35 PM
Event ID: 28
Task Category: File Block Shredding (rule: FileBlockShredding)
Level: Information
Keywords:
User: SYSTEM
Computer: dc1.Win2022.local
Description: File Block Shredding:
RuleName: -
UtcTime: 2024-04-16 03:57:35.123
ProcessGuid: {8a1a452d-2087-65de-9204-000000000500}
ProcessId: 6992
User: win2022\administrator
Image: C:\Windows\Explorer.EXE
TargetFilename: C:\Users\bosshogg\AppData\Roaming\Microsoft\Windows\Recent\logs.lnk
Hashes: SHA1=BA90632BB2CE42BB40C93CD0B2A88E1FE7E0787E,MD5=9473398C90A26774335A3F8235A5ADC6,SHA256=D876955B30350ED09A90E37713A71E649667952C318B9C6879E855CC07B39430,IMPHASH=00000000000000000000000000000000
IsExecutable: false
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Sysmon" Guid="{5770385F-C22A-43E0-BF4C-06F5698FFBD9}" />
<EventID>28</EventID>
<Version>5</Version>
<Level>4</Level>
<Task>28</Task>
<Opcode>0</Opcode>
<Keywords>0x8000000000000000</Keywords>
<TimeCreated SystemTime="2024-02-27T17:48:55.9824794Z" />
<EventRecordID>1177</EventRecordID>
<Correlation />
<Execution ProcessID="9596" ThreadID="11128" />
<Channel>Microsoft-Windows-Sysmon/Operational</Channel>
<Computer>dc1.Win2022.local</Computer>
<Security UserID="S-1-5-18" />
</System>
<EventData>
<Data Name="RuleName">-</Data>
<Data Name="UtcTime">2024-02-27 17:48:55.967</Data>
<Data Name="ProcessGuid">{8a1a452d-2087-65de-9204-000000000500}</Data>
<Data Name="ProcessId">6992</Data>
<Data Name="User">win2022\administrator</Data>
<Data Name="Image">C:\Windows\Explorer.EXE</Data>
<Data Name="TargetFilename">C:\Users\bosshogg\AppData\Roaming\Microsoft\Windows\Recent\logs.lnk</Data>
<Data Name="Hashes">SHA1=BA90632BB2CE42BB40C93CD0B2A88E1FE7E0787E,MD5=9473398C90A26774335A3F8235A5ADC6,SHA256=D876955B30350ED09A90E37713A71E649667952C318B9C6879E855CC07B39430,IMPHASH=00000000000000000000000000000000</Data>
<Data Name="IsExecutable">false</Data>
</EventData>
</Event>
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection