 Sysmon Event ID 25
Sysmon Event ID 25

25: Process Tampering
This is an event from
Sysmon.
On this page
This event is logged by Sysmon when it detects advanced process tampering attacks such as herpaderping and hollowing. In these techniques the attacker fools the OS and security products into thinking an innocuous process like Chrome was started while infact a completely differnet program like mimikatz was executed. The technique involves manipulating the process memory and files backing it in a special shell-game like sequence. This is an important for catching advanced attacks.
Free Security Log Resources by Randy
- Log Name
- Source
- Date
- Event ID
- Task Category
- Level
- Keywords
- User
- Computer
- Description
- RuleName
- UtcTime
- ProcessGuid
- ProcessId
- Image
- Type
- User
Supercharger Free Edition
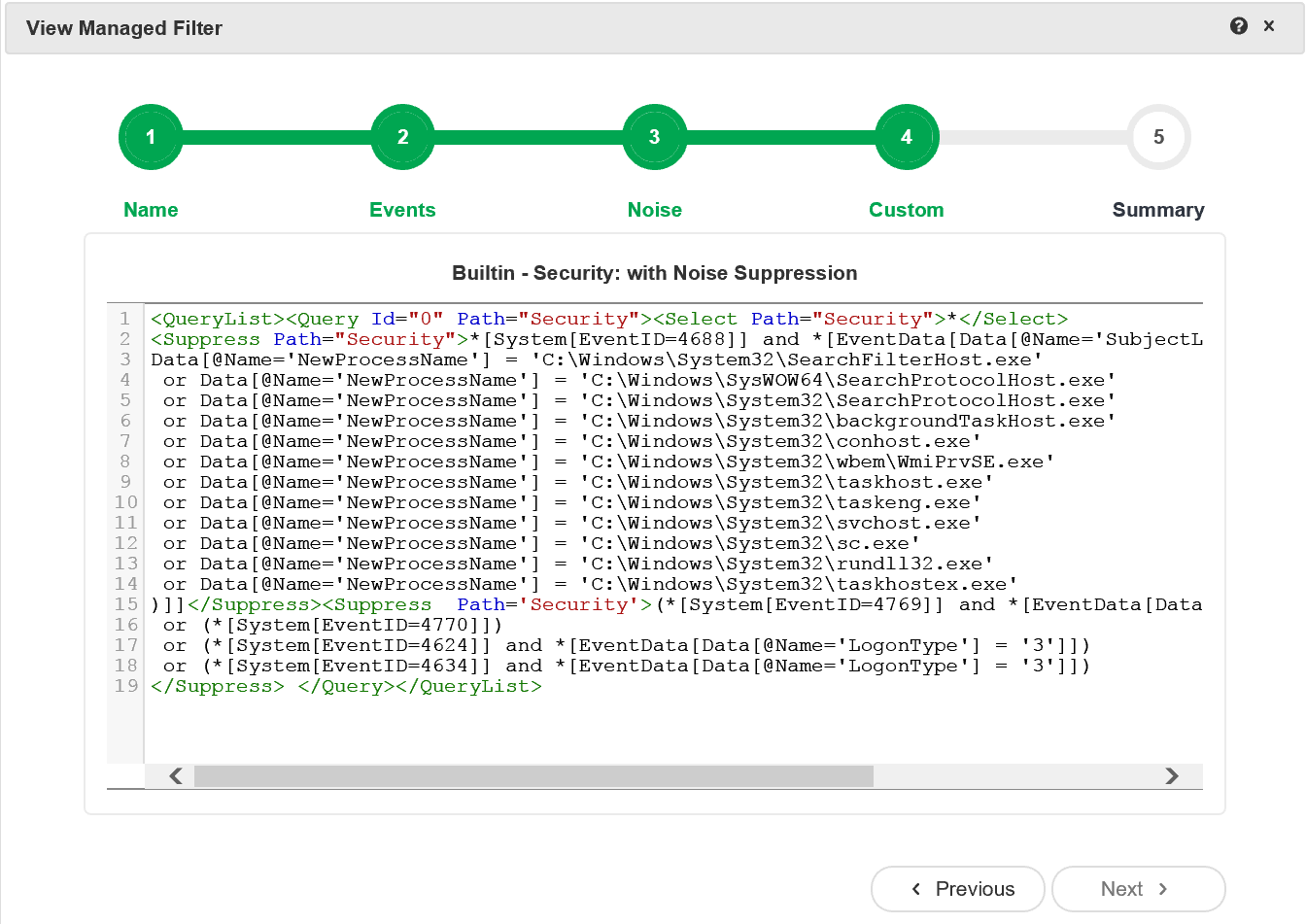
Supercharger's built-in Xpath filters leave the noise behind.
Free.
Log Name: Microsoft-Windows-Sysmon/Operational
Source: Microsoft-Windows-Sysmon
Date: 4/15/2024 8:57:35 PM
Event ID: 25
Task Category: Process Tampering (rule: ProcessTampering)
Level: Information
Keywords:
User: SYSTEM
Computer: dc1.Win2022.local
Description: Process Tampering:
RuleName: -
UtcTime: 2024-04-16 03:57:35.123
ProcessGuid: {8a1a452d-2087-65de-9204-000000000500}
ProcessId: 5824
Image: <unknown process>
Type: Image is replaced
User: win2022\administrator
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Microsoft-Windows-Sysmon" Guid="{5770385F-C22A-43E0-BF4C-06F5698FFBD9}" />
<EventID>25</EventID>
<Version>5</Version>
<Level>4</Level>
<Task>25</Task>
<Opcode>0</Opcode>
<Keywords>0x8000000000000000</Keywords>
<TimeCreated SystemTime="2024-02-27T17:48:55.9824794Z" />
<EventRecordID>412</EventRecordID>
<Correlation />
<Execution ProcessID="9596" ThreadID="11128" />
<Channel>Microsoft-Windows-Sysmon/Operational</Channel>
<Computer>dc1.Win2022.local</Computer>
<Security UserID="S-1-5-18" />
</System>
<EventData>
<Data Name="RuleName">-</Data>
<Data Name="UtcTime">2024-02-27 17:48:55.967</Data>
<Data Name="ProcessGuid">{8a1a452d-2087-65de-9204-000000000500}</Data>
<Data Name="ProcessId">5824</Data>
<Data Name="Image"><unknown process></Data>
<Data Name="Type">Image is replaced</Data
<Data Name="User">test\bosshogg</Data>
</EventData>
</Event>
Top 10 Windows Security Events to Monitor
Free Tool for Windows Event Collection