«
Work Smarter – Not Harder... |
Auditing Privileged Opera... »
Tracking removable storage with the Windows Security Log
Mon, 02 Jan 2017 10:46:36 GMT
With data breaches and Snowden-like information grabs I’m
getting increased requests for how to track data moving to and from removable
storage such as flash drives. The good
news is that the Windows Security Log does offer a way to audit removable
storage access. I’ll show you how it
works and since the sponsor for this post, EventTracker, has some enhanced
capabilities in this area I’ll briefly compare native auditing to
EventTracker.
Removable storage auditing in Windows works similar to and
logs the exact same events as File System auditing. The difference is in controlling what
activity is audited.
To review, with File System auditing, there are 2-levels of
audit policy. First you enable the Audit
File System audit subcategory at the computer level. Then you choose which folders you wish to
audit and enable object level auditing on those folders for the users/groups,
permissions and success/failure results that need to be monitored. For instance you can audit Read access on
C:\documents for the SalesReps group.
However Removable Storage auditing is much simpler to enable
and far less flexible. After enabling
the Removable Storage audit subcategory (see below) Windows begins auditing all
access requests for all removable storage. It’s equivalent to enabling auditing Full Control for Everyone.
As you can see auditing removable storage is an all or
nothing proposition. Once enabled,
Windows logs the same event ID 4663 as for File System auditing. For example the event below shows that user rsmith
wrote a file called checkoutrece.pdf to a removable storage device Windows
arbitrarily named \Device\HarddiskVolume4 with the program named Explorer (the
Windows desktop).
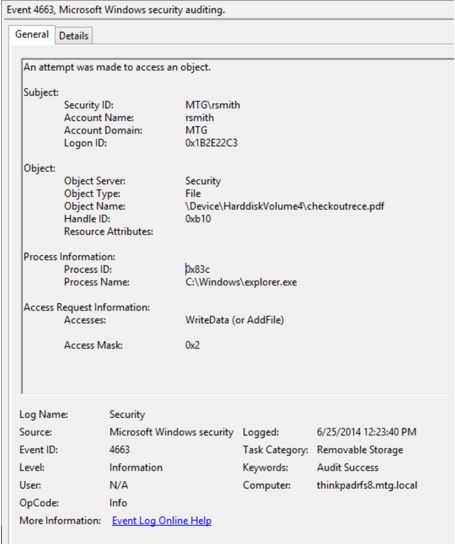
How do we know this is a removable storage event and not
just normal File System auditing? After
all it’s the same event ID as used for normal file system auditing. Notice the Task Category above which says
Removable Storage. The information under
Subject tells you who performed the action. Object Name gives you the name of the file, relative path on the
removable storage device and the arbitrary name Windows assigned the device the
first time it was connected to this system. Process information indicates the program used to perform the
access. To understand what type of access
(e.g. Delete, Write, Read) was performed look at the Accesses field which lists
the permissions actually used.
If you wish to track information being copied from your
network to removable storage devices you should enable Audit Removable Storage
via group policy on all your endpoints. Then monitor for Event ID 4663 where Task Category is Removable Storage
and Accesses is wither WriteData or AppendData.
As you can see Microsoft took the most expedient route
possible to providing an audit trail of removable storage access. There are events for tracking the connection of devices – only the file
level access events of the files on the device. These events also do not provide the ability to see the device model,
manufacturer or serial number. That
device information is known to Windows – it just isn’t logged by these events
since they captured at the same point in the operating system that other file
access events are logged. On the other
hand, EventTracker’s agent logs both connection events and information about
each device. In fact EventTracker event
allows you selectively block or allow access to specific devices based on
policy you specify. I encourage you to
check out EventTracker’s
enhanced abilities.
This article by Randy Smith was originally published by EventTracker”
https://www.eventtracker.com/newsletters/tracking-removable-storage-windows-security-log/
 email this
•
email this
•
 digg
•
digg
•
 reddit
•
reddit
•
 dzone
dzone
comments (0)
•
references (0)
Related:
Auditing Privileged Operations and Mailbox Access in Office 365 Exchange Online
Understanding the Difference between “Account Logon” and “Logon/Logoff” Events in the Windows Security Log
5 Indicators of Endpoint Evil
Severing the Horizontal Kill Chain: The Role of Micro-Segmentation in Your Virtualization Infrastructure
Comments disabled
powered by Bloget™