Vulnerability scanning has its place but I’ve often found that it produces a mountain of data with little guidance for prioritizing updates other than a relative high/medium/low risk rating of the exploit itself and of the device’s value.
Many of the vulnerabilities reported are mitigated by other compensating controls that the scanner is not aware of. The most frequent compensating control is network restrictions.
For instance, a given high value server, like a Hyper-V server, may be vulnerable to a Remote Desktop Protocol Exploit and is dutifully reported by your vulnerability scanner. But that Hyper-V system happens to be on a highly isolated network segment where RDP connections are only admitted from a trusted jump box.
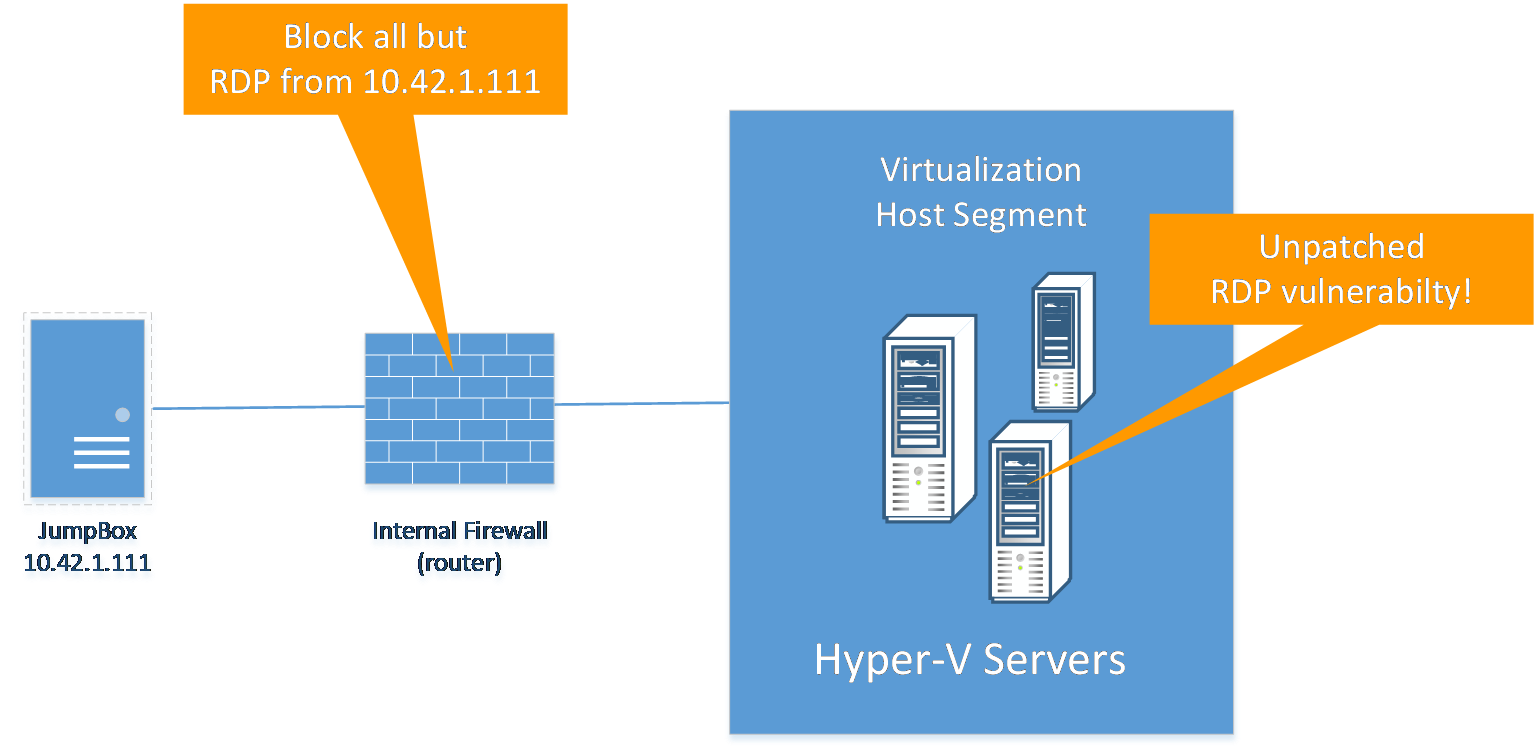
So, to get an accurate picture of vulnerability analysis you need to consider network-based controls.
And that’s not just from the point of view of reducing the relative priority of reported vulnerabilities because of compensating controls. While network restrictions may be effective they are also complicated, subject to change and managed by a network team while servers are managed by their own team. A typical organization has many firewalls if you count routers, managed switches and everything else with a network access control list. It's not at all unusual to have tens of thousands, even more than a hundred thousand, rules if you combine all your network devices.
So, taking into account network access when analyzing vulnerabilities can also push up the relative risk of a given vulnerability. Taking the earlier example a step further, what if over the course of time that jump box is replaced with a privilege session management appliance on a different IP address? The ACL is never updated to remove the exception allowing the jumpbox to RDP into the Hyper-V host segment and that IP address is re-used for some other device such as maybe a Linux server for “playing around with” by IT admins.
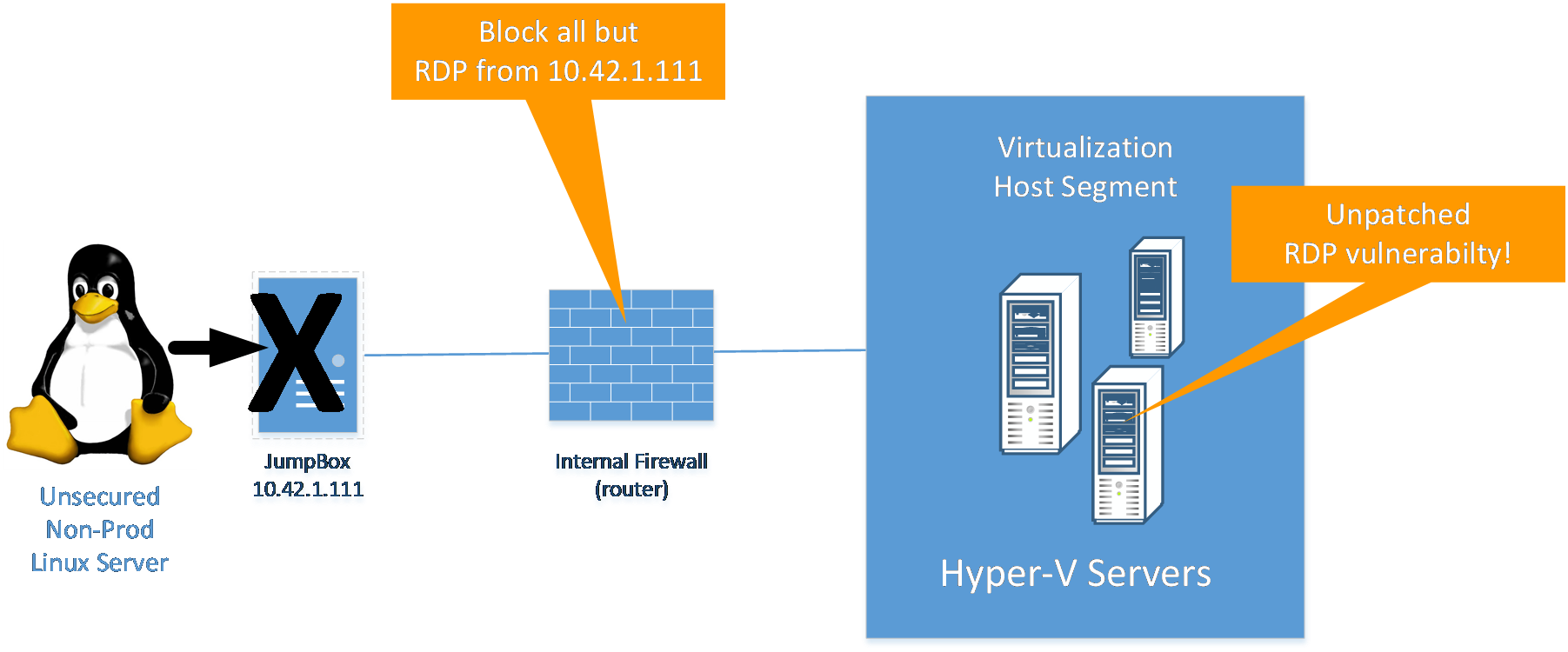
Now that vulnerability on the Hyper-V servers becomes a much bigger risk.
In this real training for free event, I will explore how to correlate vulnerability scans with network access path data to discover your biggest risks while helping de-prioritize those vulnerabilities that present the least risk when taking into account the current state of your routed network.
My sponsor, FireMon, are the experts on analyzing firewall rules to optimize network traffic and security and Matt Dean, VP of Product, will join me to share what they’ve learned about correlating vulnerability scans with network path analysis and will briefly show you how FireMon can even visually lay vulnerability data on top of route intelligence to help you see the risks.
Please join me for this real training for free event.